Yes, you can be anonymous online. At least under the right conditions, but it’s not necessarily easy. Your everyday identity is constantly being tracked by accounts you’re logged into, and third-party advertising companies hoping to better target ads. That means your favorite browser is usually filled with trackers to keep tabs on what you’re doing online.
Plus, who knows what’s going on with your internet service provider, passive (or active) government data collection, and all kinds of other interlopers? The bottom line is you have to take deliberate steps to ensure a modicum of anonymity online.
That said, if all you want is an anonymous email account that no one in your professional or home life knows about, that’s not as hard. Still, all it takes is one slip up by logging in to the email account before you secure your connection, or accessing your non-anonymous identity at the wrong time, and your identity could be revealed.
This tutorial will walk you through the necessary steps, and depending on how far you want to take it, you can either use all of the advice within or pare it down to only the parts you need. We’ll explain why each step is necessary to help guide your decisions.
Step 1: Get an anonymous workspace
The best thing to do if you want to stay really anonymous is to have a separate digital work space that is only used for your secret identity. That way there’s no risk of crossover between your everyday accountant self, and your anonymous whistleblowing/Mr. Robot identity.
If you just set up an account using a regular browser on your everyday machine all it will take is someone nosing around in your PC and oops! there goes your anonymity.
Here are some options.

Tor Project
Level 1: Install the TOR browser on a USB thumb drive. If your stakes are pretty low (i.e. if your account is discovered it’s not the end of the world) then TOR running off a USB drive may be all you need. The TOR browser is a version of Firefox that connects to the onion router (TOR) network. This system passes your internet connection through multiple nodes (computers) before putting you on the open internet. When using TOR your real IP address is obscured. Plus, by default the TOR browser doesn’t save your browsing history, keeping your activity secret. To keep TOR as secure as possible check out the Tor Project’s tips on what to do to stay as secure and private as possible online.
Also check out our tutorial on the TOR browser for more information.
Level 2: More advanced users could run an entire operating system such as the privacy-protecting Linux distribution Tails off a thumb drive. This is like having a completely separate computer without having a second physical device. Again, this is all about putting a firewall between your real identity and your anonymous account.
Level 3: If you are ultra-paranoid or getting found out means non-life threatening disaster then consider a completely separate laptop that is only used for your secret identity. It’s preferable to pay for your device in cash, or with a throwaway visa gift card to avoid having the laptop connected back to your office-dwelling persona. The laptop should be running a variant of Linux that is encrypted, but if you must use Windows 10 make sure you activate your machine with a local account, turn off all possible tracking methods during setup, and don’t use Cortana. Also, don’t install unnecessary software onto this device and don’t log in to accounts from your regular life no matter what. The idea is to have as little extra information on this laptop as possible. Extra applications and mixing your anonymous life with your actual life are big “no-nos.” Also, don’t forget to put some tape or a piece of paper over your webcam. It’s ultra-paranoid, but even Mark Zuckerberg does it.
Step 2: Location, location, location
 Hanohiki/Getty Images
Hanohiki/Getty ImagesYou never want to access your secret identity from home or work. This is just a bad idea since there’s a chance of revealing an Internet Protocol (IP) address that could be traced back to you. Again, it would have to take some pretty advanced sleuthing to find this, but part of being anonymous is to make sure nobody knows where you really are. Keep your anonymous activities to a local coffee shop, a library, or somewhere else that offers public Wi-Fi. If you’re really paranoid, it’s probably also a good idea to pick somewhere that isn’t too close to your everyday locations.
For the super paranoid: Another important note is that other devices you’re using can also give you away. To keep things as separate as possible leave your phone at home, or at the very least turn it off and (if you can) take out the battery.
Step 3: Use TOR or a VPN (but not really)
Once you’ve got a location that isn’t your home or work from which to do your shadowy emailing, it’s time to connect to the internet. But wait! Before you do that, you need to either use the TOR network or a high-quality VPN.
If you are already using the TOR browser via a USB thumb drive then skip over this part, because you’re already doing it. For everyone else, we’d still recommend using TOR and not a VPN, because the beauty of the TOR network is you don’t have to trust anyone. TOR works by running your encrypted connection through multiple servers before letting you out onto the open network. That way it’s much harder to trace you back to your real location, and only the final server that lets you out onto the web truly has a shot at spying on your activities—barring unforeseen exploits, that is.
 Thinkstock
ThinkstockIf a VPN is a better option for you, however, choose a VPN that accepts cash, has a long track record of defending user rights, and then use TOR anyway.
Seriously, your best shot at anonymity for the purpose of using a secret email account is TOR. If you pay with a credit card for your VPN, you’re traceable, if the VPN is somehow compelled to track you, you are also at risk. True, these are all worst case scenarios, but it’s the principle that matters. Stay as anonymous as you can, use TOR.
But TOR isn’t a magic bullet by itself. The TOR browser uses the browser extension HTTPS everywhere from the Electronic Frontier Foundation by default. That extension will secure your connection over SSL/TLS between the exit node and the website you want to visit. That should be enough to keep any potential snoops out of your business.
Keep in mind that when using the TOR browser, only that app is connected to the TOR network. If you start using the Spotify desktop app to stream music at the same time it won’t happen over TOR.
Step 4: Create an email account
IDG
There are tons of anonymous email options out there such as Guerrilla Mail and Secure-Email.org. We’ll talk about that in a bit, but we’re going to assume you need a standard email address with an inbox, sent folder, and all the rest.
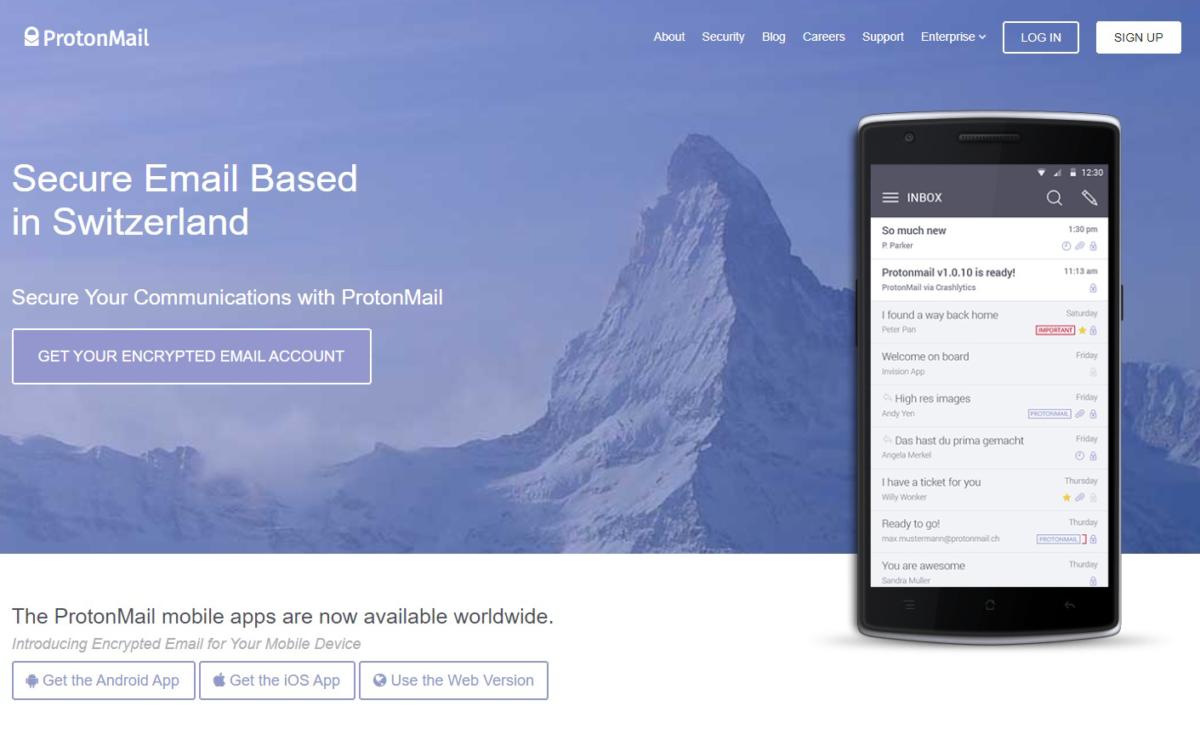
We’d recommend using ProtonMail. It’s one of the few well-known email services that you can use without providing some back-up identification like a phone number or secondary email. Plus, ProtonMail is encrypted by default, and it has a TOR-accessible version of its site at https://protonirockerxow.onion/ making it a solid choice.
Step 5: Go forth and remember these tips
Now that you’re connected through TOR on a separate work space, and you’ve got your email set up, it’s time to get messaging. When you write email be careful not to say anything that might reveal your actual identity, and never connect to anything in your real life when using your special anonymous setup.
It’s also a good idea to memorize the username and password for your anonymous email account. Don’t put them in the password manager that’s part of your regular life, don’t leave sticky notes on your laptop that can fall off, and don’t use your ProtonMail username and password anywhere else, ever.
If you need a lesson in why this is important read about how law enforcement caught up with Silk Road founder Ross Ulbricht. It all started with an obscure username that Ulbricht had used years ago and that he’d connected to his actual identity. Remember, all it takes is one slip-up to undo all your privacy-protecting steps. Also, don’t start a digital black market dedicated to selling drugs and weapons—that’s just asking for trouble.
Bonus section: Anonymous email services
When all you need to do is send a single anonymous email, then conditions are different. First, you don’t necessarily want to bother with a secondary laptop. So let’s assume you’re using the TOR browser on a USB stick, but you’re still not connecting from home or the office.
IDG
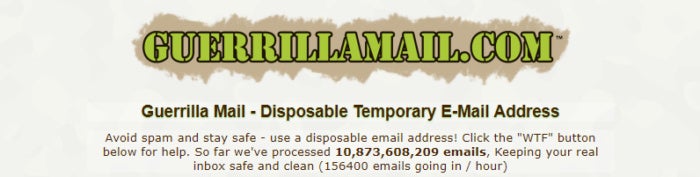
So what then? Visit GuerillaMail.com. You’ll get a disposable temporary email address that will last forever. Anyone can send an email message to this address, but the messages last in the inbox for only one hour. This is a handy service if all you’re going to do is send a single email with no response or maybe a single response required, but it’s not the greatest option for trading multiple responses.
The thing is anyone who has the GuerillaMail address you’re using will be able to monitor the inbox since there’s no username or password required. GuerillaMail gets around this by supplying two email addresses: the actual email address that gets you to the inbox, and a “scrambled” address that you give out to others. It’s a neat trick, but it’s already adding complexity to something that doesn’t need to be this hard. We’d recommend just keeping a secret identity on a standard email service. Besides, Guerrilla Mail is really about reducing spam in your already overflowing inbox, not necessarily maintaining a secret email account.
To comment on this article and other PCWorld content, visit our Facebookpage or our Twitter feed.
Source: https://www.pcworld.com/article/3340824/how-to-send-anonymous-emails.html#tk.rss_howto