Say hello to Motorola's four budget champs of 2019.

Ever since the first Moto G was released all the way back in 2013, Motorola's G series of smartphones has been one of the go-to options for people that want a phone that looks great and performs well while spending a fraction of what typical flagships cost.
For 2019, Motorola is returning with the Moto G7 lineup and launching more G phones at once than ever before.
Whether you're looking for official specs, our initial impressions of the phones, or anything else, here's everything you need to know!
March 15, 2019 — You can now pre-order the Moto G7 Power for $250
Right on schedule, Motorola has opened pre-orders for the Moto G7 Power in the United States.
The phone costs $249.99, and to sweeten the deal a little bit, all pre-orders come with a $20 credit towards your next purchase on Motorola's website.
Following pre-orders, the Moto G7 Power will officially launch on March 22.
See at Motorola
March 11, 2019 — Moto G7 Play and G7 Power U.S. pre-orders begin this month
The Moto G7, Motorola's flagship budget phone for 2019, officially went on sale in the U.S. in February. Later this month, you'll be able to pre-order its two siblings — the Moto G7 Play and G7 Power.
The Moto G7 Play has weaker specs across the board compared to the regular G7, but in turn, also gets a price tag of just $200. The G7 Power comes in at the middle for $250 and gets its name thanks to the truly massive 5,000 mAh battery inside it.
Pre-orders for the Moto G7 Power begin on March 15 with an official launch following on March 22. As for the G7 Play, you'll be able to pre-order it starting March 29 with full sales beginning April 5.
Both phones will be sold at Motorola, Amazon, Best Buy, and B&H.
Check out our hands-on coverage

Motorola's Moto G phones are consistently some of the best in the budget smartphone space each year, and with the G7, things aren't any different. In fact, they may be better than ever.
The Moto G7 brings a lot to the table for its modest $300 price tag. The build quality is fantastic, its large display with minimal bezels is a treat to use, and it works on every carrier in the U.S.
You can check out our full review of the regular G7 below, in addition to some initial hands-on impressions of the G7 Power and G7 Play.
Moto G7 review: The right price to pay
Moto G7, G7 Power and G7 Play Hands-on: Why even buy an expensive phone anymore?
There are four different models to choose from
The Moto G7 series consists of four different phones. In order of least to most expensive/powerful, they include:
Moto G7 Play
Moto G7 Power
Moto G7
Moto G7 Plus
The G7 Play is clearly at the bottom of the barrel and delivers pretty basic specifications and features for less than $200. As the name suggests for the G7 Power, this is a phone designed around delivering unrivaled battery life.
Motorola's base G7 falls in the middle of everything else with a nicer design, a smaller notch, and improved performance.
Lastly, the G7 Plus aims to deliver much-improved cameras, stereo speakers, and incredibly fast 27W charging.
Here are the specs

Moto G phones never have the most impressive specifications, but they're good enough to deliver an experience that's still enjoyable for the end user.
Here's a quick snapshot of what we have to look forward to with the Moto G7 lineup.
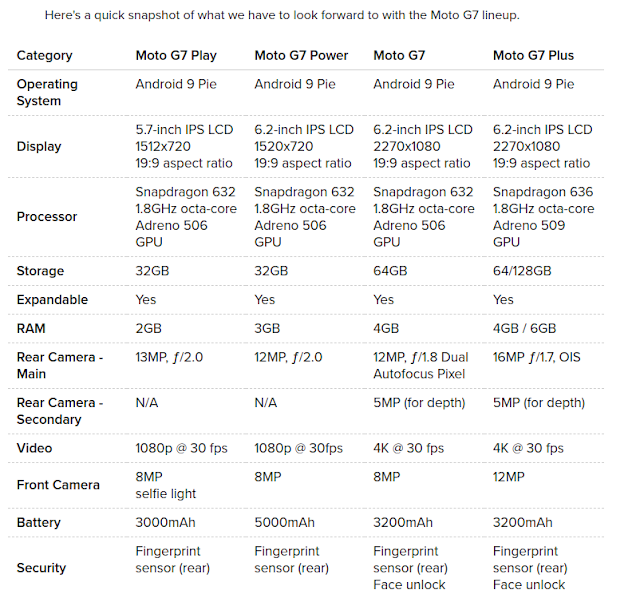
For the entire spec list, check out the link below 👇
Moto G7 specifications: 2019 is a good year for budget phones
When and where can you buy the phones?

Finally, the most important section of this entire post — When will you be able to buy the Moto G7 phones and how much will they cost?
Moto G7 Play — $199
Moto G7 Power — $249
Moto G7 — $299
Unfortunately, the Moto G7 Plus will not be making its way to the United States.
The regular G7 is available for purchase now, the G7 Power is currently up for pre-orders, and initial sales for the G7 Play will begin on March 29
See at Motorola
This post may contain affiliate links. See our disclosure policy for more details.
Source: https://www.androidcentral.com/moto-g7

 Hanohiki/Getty Images
Hanohiki/Getty Images Thinkstock
Thinkstock