Torrenting is a great way to get expensive software or restricted content without cost or limit. Whether you want to download movies, music, games, ebooks, or premium apps, you don’t have to pay anything on the best torrent sites.
However, you cannot test dozens of platforms to find the perfect one for you. Plus, many free services that offer TV series, movies, e-books, or cracked software contain malware. Users who download torrents from these websites should continue to exercise caution. To help your research, we’ve tested hundreds of sites and compiled a list of the top 31 torrent websites that offer secure content.
DISCLAIMER: This guide only provides information. Torrenting itself isn’t illegal, but downloading or sharing content from websites hosting copyrighted content can be. Note that all the sites listed here provide content without legal rights and may contain malware. For this reason, ExtremeVPN doesn’t promote any of such platforms. If you still want to access them, make sure to use a VPN and antivirus software.
The Best Torrent Sites in 2024 – Quick List
Running late? Here is a quick list of the 31 most popular torrent platforms that still work in 2024:
- 1337X: One of the most visited torrent sites, having a convenient interface and a wide range of content.
- YTS: Specializes in providing high-definition movie torrents where videos are compressed as small files without sacrificing quality.
- TorLock: The website aims to highlight only the trusted torrents so that the users can get trustworthy data.
- AniDex: An anime-focused torrent tracker that offers various Japanese animations, including animated series and films.
- TorrentDownloads: Complete site that includes all possible videos, films, games, and other programs.
- EZTV: Famous for its simple and well-structured interface.
- FitGirl Repacks: Offers repackaged versions of popular games with smaller file sizes.
- SolidTorrents: A new website with a smooth interface, offering quality content.
- iDope: A widely known platform with a convenient user interface that provides extensive results.
- TorrentGalaxy: Boasts an active and responsive member population.
- BTDigg: A decentralized service that has an exceptional way of finding torrents.
- YourBittorrent: A well-known website that allows users to search for and download files easily.
- GloTorrents: Offers thousands of movie files, TVE series, computer games, etc.
- Skidrow & Reloaded: Specializes in releasing repacked versions of famous video games.
- isoHunt: A torrent site that has been used for a long period to help people find and obtain files from different categories.
- The Pirate Bay: An established platform that hosts unlimited magnet links and files for various resources.
- RARBG: Known as a reputable source for quality content, RARBG has a strong online presence.
- Kickass Torrents: A great website famous for its huge collection of files and ease of use.
- Torrentz2: A torrent search aggregator so users can view them all concurrently.
- LimeTorrents: Provides all types of content, including movies, TV shows, games, or other files downloaded and shared.
- Torrends.to: Collects information from many sources so that web admins can get and dispense with the files of games.
- Torrentfunk: Offers verified downloads and a user-friendly interface.
- Nyaa.si: One of the most frequently used torrent sites with many Japanese anime series and films to offer.
- BitPort: A browser-based BitTorrent downloader that helps to access torrent files online.
- MyAnonaMouse: A private tracker focusing on ebooks, audiobooks, and learning materials.
- RuTracker: A Russian torrent site that offers hundreds of entertainment media categories.
- MagnetDL: Offers many magnetic links and files to download.
- TorrentLeech: A private torrent platform that has a pool of carefully selected files and active user forums.
- Demonoid: Various files are offered on this BitTorrent tracker supported by crowdsourcing.
- IGGGAMES: Home for finding crack software downloads and several game titles, all free of charge.
- Public Domain Torrents: A free website offering many classic films for users.
1.1337x is one of the most well-liked torrent websites. The site is almost always featured whenever someone gathers the list of popular torrent trackers.
Founded in 2007, 1337x started its operations in many countries, but it is prohibited in the UK, Australia, Austria, and Ireland. It has an advanced user interface with accurate navigational directories.

It also has an enormous collection of torrents in many categories. So, everything you need to download, whether a game, a movie, or premium software for free (with activation), can be found here.
There aren’t any content restrictions when using this torrent tracker. It contains several links to the content it offers, including magnet links, making it easy to get what you want. During our testing, we found that new torrents are added to the website every hour, so you can appreciate the level of diversity offered here.
2.YTS/Yify Torrents was a peer-to-peer release group known for distributing movie content as free downloads through BitTorrent. Whether it’s a classic, hard-to-find film or one of the latest, you will likely find it here, making YTS the greatest website for torrenting high-quality films.
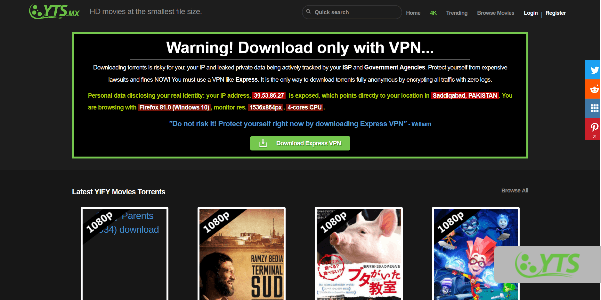
The site has a simple-to-use interface that makes it easy to navigate. Plus, it has a functional search bar you can use to find a specific title you have in mind. If you’re not sure what to watch, you can also explore the “Trending” section available on top. YTS is the second most-visited torrent website, just behind Pirate Bay’s popularity.
As recently discovered, the platform has consciously joined the anti-piracy system by providing law firms with user data. Following this, we strongly advise all users to use a reliable VPN before visiting the website. You can also explore other options like YTS/Yify.
3.Torlock is another great torrent site for movies and TV shows. It is a secure platform to visit if you’re new to torrenting. Since its establishment in 2010, it has operated without complications and has seen only a few bans.
Users from many nations can easily access the site. However, if you’re from Australia, the United Kingdom, or India, you will need to connect to a VPN like ExtremeVPN to use Torlock since it is banned in these countries.
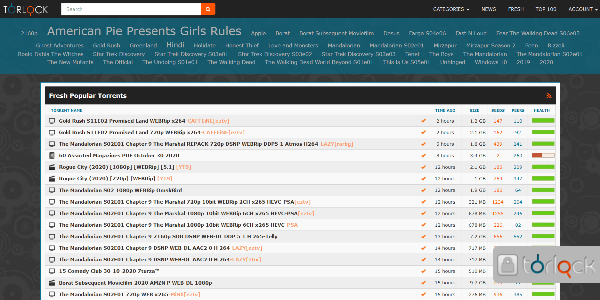
TorLock’s no-fake torrent behavior helped it place in the top 10 on our list. You won’t have to worry about malware when downloading verified and secure torrents from this source. Plus, the platform pays $1 to anyone who reports fake torrents on the website. This shows the TorLock team’s commitment to maintaining the site’s security.
The website’s database size is comparatively smaller than that of other sites. Some popular niches of the website include TV series, anime, music, movies, and e-books. The platform also offers difficult-to-find content.
4.AniDex ranks among one of the best torrent sites for anime. The website is updated frequently, and you can expect to find pictures, audio, games, and manga on the site for free. It has an easy-to-use interface and offers anime fans a limitless free collection of independent torrents.
During our tests, we found the website to be accessible from everywhere in the world. It is, therefore, not geo-blocked. Anidex also has a Quick Search bar that will catch your attention. It offers manga torrents with files in the .cbz format and anime content.
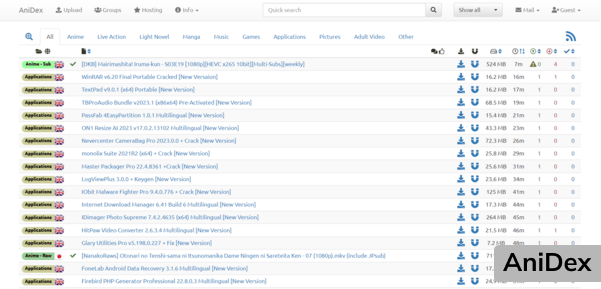
If you love reading novels, you can find light novels in both Japanese and English here. Additionally, the platform provides specialized tabs for serious gamers, enabling them to download different games anytime. It also provides a huge selection of anime subtitles in Arabic, English, and Spanish, among other languages.
The site has many seeders for popular anime torrents. But there might be fewer people seeding other, different files. Hence, a few torrent services can rival AniDex in terms of anime content.
5.TorrentDownloads is a P2P file sharing platform that allows users to share and download large files more efficiently. With a vast database of over 16 million torrents, it deserves to be among the best torrenting sites. The site makes it easy for you to locate the movie, TV show, ebook, or software you want.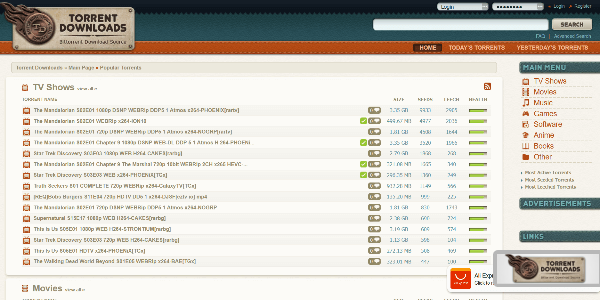
Since its establishment in 2007, TorrentDownloads has maintained its credibility by keeping a low profile. Users worldwide can easily access the site because it has helped avoid most bans. Users in the UK, however, might run into issues because the site is prohibited there. However, you can get around these restrictions with a working, secure VPN like ExtremeVPN.
6.EZTV offers a comprehensive option for those who enjoy downloading television series. Since it’s a TV torrent site, you won’t find anything else. It primarily sources direct and magnet torrent URLs for all popular and uncommon TV series. If you want to explore other content, such as online books, movies, or music, there are many EZTV alternatives available online that you can check out.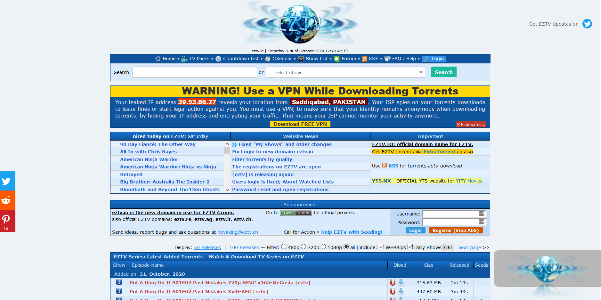
The website first launched in 2005, and it was working fine. Plus, it was free of ads. However, in 2015, the original platform ceased working, and a few of its ad-displaying mirror sites appeared online. To ensure safety, exercise caution while using such sites, as they may not be safe to access.
You may use the site to download your favorite shows, an e-book torrent, or anything else you require, though, if you use caution when surfing (for example, by using an ad blocker and antivirus to cut through the chaff).
7.Fitgirl Repacks is a well-known torrent website for finding and downloading games. Unlike other platforms on this list, the moderator of this site uploads video game torrents for users. However, there’s a limitation—members can only download the content; they are unable to upload it.
Fitgirl Repacks offers many games. The website’s UI is straightforward, and the search bar lists the most recent game torrents available that users can see at the head of the page. That’s not just all. You won’t face any intrusive pop-ups or dangerous advertisements. This makes it easy for you to download files without any interruptions.
While being a popular gaming destination, the website provides visitors with free copyright content. This is considered piracy and is prohibited in most states. Hence, we advise against it.
8.SolidTorrents will spare you the trouble of searching multiple torrent websites. It’s a standard metasearch engine with indexed torrents from numerous reliable sources and a simple interface. Therefore, whatever content you seek, you can find it here.
The website’s UI could have been improved further. However, it works well for torrent searching. The site had already been flagged as dangerous since it detected malware on certain pages. Thus, we strongly advise anyone visiting this website to set up a robust VPN like ExtremeVPN and anti-malware software on their device.
9. iDope is a relatively recent addition to the torrent industry. The website was launched in 2016 and is a great torrent search portal that offers direct magnet URLs to secure files. It debuted live as a memorial to KickAss Torrents after the latter was shut down, also mentioned in its logo. iDope keeps working as planned, even though KickAss Torrents is up.
iDope is banned in India, Australia, the UK, and Denmark. However, you can always get around this limitation with a VPN. Users can still view it through a few mirror URLs.
While reviewing the platform, we found that the iDope database is smaller than many torrent sites. However, it still functions best as the essential files are downloaded quickly. Furthermore, the database is updated more often, so you may also find the newest films and TV series here.
10. TorrentsGalaxy is another multifunctional torrenting platform. It has a huge library of torrents that source material from all the main categories, as the name implies. Anything you can think of, including movies, TV series, games, software, music, e-books, apps, and even online courses for skill development—this website has the torrent link for it.
Its layout is simple, easy to browse, and engaging. You can also make a fast search and find the torrent links for the content you’re looking for. The search results also include the file size, time and date of upload, uploader identity and status, and seeder/leecher ratio. An unsuspecting user might easily identify the correct link with the help of these facts.
More details here: https://extremevpn.com/blog/best-torrent-sites/
Another great article:The 21 Best Torrent Sites for 2024:
https://vpnoverview.com/privacy/downloading/best-torrent-sites/